Cara-cara nya :
1) Buka windaows task manager ( Tekan CTRL+ALT+DEL ) , masuk bahagian processess.
2) Matikan process wgatray.exe dengan menekan button End process.
3) Selepas itu,restart windows dan sebelum masuk windows,tekan button f8 pada keyboard anda dan pilih untuk masuk melalui safe mode.
4) Masuk ke dalam folder c:\windows\system32 dan folder c:\windows\system32\dllcache,cari file wgatray.exe. Kalau jumpa,deletekan file tersebut dalam kedua-dua folder tu.
5) Lepas tu,click button Start Windows kt sebelah bawah kiri skrin monitor anda, amik Run, taipkan regedit. Pastu cari HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify, kalau jumpa, deletekan folder wgalogon.
6) Restart windows lagi sekali.
7) Siap !
Pesanan : Aku bukan nak sokong piracy(pirate ) dengan ajar benda ni,tapi face the truth la,aku belajar lagi, mana mampu nak beli windows yang original.. betul tak kawan-kawan ? hehe ..
Selamat mencuba
^o^ hohoho
Saturday, November 10, 2007
Friday, November 9, 2007
Definition of XSS
::: What is Cross Site Scripting (XSS)? :::
XSS is simply tricking a web server into presenting malicious HTML to the user. Usually the intent is to steal session information.
Scripts may also be used to change the contents of web pages in order to displays false information to the visitor, and it may be used to redirect forms so that secret data are posted to the attacker's computer. XSS generally attacks the user of the web application, not the application itself. The attacks are possible when the web application lacks proper output filtering.
XSS is simply tricking a web server into presenting malicious HTML to the user. Usually the intent is to steal session information.
Scripts may also be used to change the contents of web pages in order to displays false information to the visitor, and it may be used to redirect forms so that secret data are posted to the attacker's computer. XSS generally attacks the user of the web application, not the application itself. The attacks are possible when the web application lacks proper output filtering.
Thursday, November 8, 2007
Learning Microsoft Access
Access provides a powerful yet comfortable environment in which you can manage your information. Using Access, you can tame even the most difficult data-management tasks. This chapter is the first step in your journey. Here you will learn basic terms, as well as how to start and exit Access. You will also learn how to get help and even catch a glimpse of what you can do with Access.
By the time you finish this chapter, you will understand the following key concepts:
*What a database is
*How tables, forms, and queries relate to a database
*What records and fields are
*How to start Access
*The parts of the Access environment
*How Wizards can help you
*How to get help when using Access
*Possible uses for both databases and Access
*How to exit Access
1. Getting Started with Access
Access Terminology
Before you dive into the Access environment, there are a few terms with which you should be familiar. As such, we'll discuss these terms now and make sure you understand them.
What is a Database?
A database is simply a collection of related information. For example, if you gathered together all your photographs, you would have a database of photographs. If you collected all your photographs that included your dog, you would have either a more targeted database or a subset of your larger database.
If your database is small (for example, your home insurance policies), you can probably manage the information manually. In such instances, you might use a traditional management method such as a card file or a simple list on a piece of paper. However, as the database becomes larger, your management task becomes more difficult. For example, it would be virtually impossible to manually manage the customer database of a large corporation. This is where your computer and a database management system (DBMS) come in handy. DBMS software (such as Access) lets you manage large amounts of information quickly and easily.
In Access, a database consists not just of information, but also the tables into which the information is organized. Access databases also contain related queries, forms, reports, and programming instructions. Because these terms deserve further definition, they are covered in the following sections.
What is a Table?
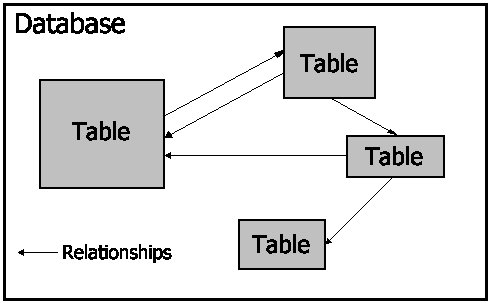
In Access, tables contain the actual information in your database. There can be more than one table in a database. The information in each table can relate to information in other tables in your database. For example, you might have one table that contains a record of all the door locks in your building. In the same database, another table might have a list of all the keys for those locks. Still another table might contain the names of all the people who have the keys. All three tables contain related information, so they belong to the same database. Figure 1-1 depicts the relationship between the tables and this database.
 Your first step in creating a database is to determine the information you need. Next, you will use Access to design a table to hold the information. Figure 1-2 illustrates the Design view of Access. You use Design view to specify the framework used for each of your table entries.
Your first step in creating a database is to determine the information you need. Next, you will use Access to design a table to hold the information. Figure 1-2 illustrates the Design view of Access. You use Design view to specify the framework used for each of your table entries.
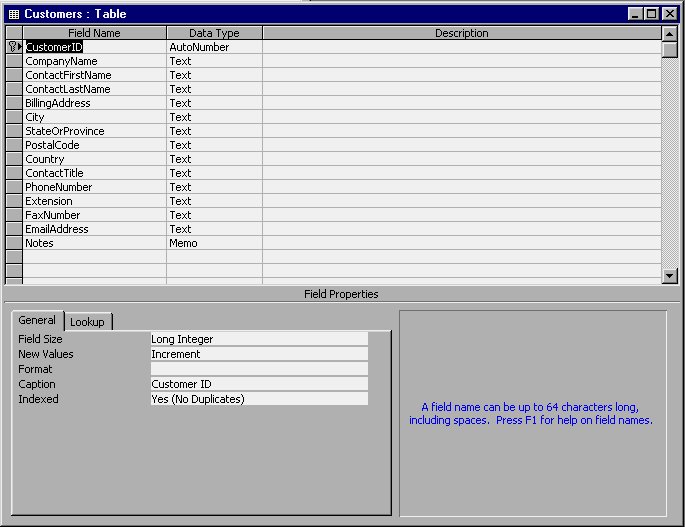 Figure 1-2 Design view for a table in Access.
Figure 1-2 Design view for a table in Access.
After you design your table or tables, you will use Datasheet view to enter and examine (view) your data. Figure 1-3 illustrates how your data may appear in Datasheet view mode.
img src="http://www.learnaccessnow.com/figs/fig0103.jpg"
Figure 1-3 Datasheet view for a table in Access.
What is a Query?
When you work with large databases, there will be times when you will want to work with specific pieces of your data. For example, if you have a company database, you may want to view the names of all your customers who reside in New York. On such occasions, you would form a query.
A query defines which database information you want to view. Think of a query as a question you ask the database, such as "Who are the customers that reside in New York?"
For example, if your database contains the names of all your customers who have purchased a particular product, your query might request a list of only those customers that made over a certain income. Another query might request only those customers with children. Essentially, a query limits or filters the information in a database. When you use a query as a filter, Access displays only information that satisfies the query.
Why would you use queries? Specifically because you want to work with only a part of your database. Queries make it easy for you to work with only those records that fit a particular criteria. Access lets you get as broad or as specific or as complex as you want in the queries you develop. You will begin to learn about queries in Chapter 6, "Using Queries to Examine Your Data."
What is a Form?
A database exists to store information. After you determine the information your database will contain, you will need to enter the data. Later, you may want to examine, add to, or change that data. Although you can use the Datasheet view to accomplish each of these tasks, you may want instead to create a custom display screen that lets you enter, view, and edit information.
Within Access, custom display screens are called forms. Using forms, you can both display the information in a table and add buttons, text boxes, labels, and other objects that make data entry much easier. Earlier, in Figure 1-3, you saw what a table looked like as a Datasheet. Figure 1-4 shows an example of a form used to input information into the same table. Notice how using the form provides a better interface for the user.
img src="http://www.learnaccessnow.com/figs/fig0104.jpg"
Figure 1-4 An example of a form used to enter information in a table.
What is a Record?
A record is a single block of information, such as employee or customer data. A table is made up of many records. For example, if you have a table that contains information about your baseball card collection, a record is the specific information about a single baseball card. Sometimes, records are referred to as rows because, within a table, Access represents individual records as rows.
What is a Field?
Just as tables are made up of records, records are made up of fields. A field is the smallest piece of information in a database. For example, if you have a table containing your phone list, each record represents a different person or business in that list. In turn, those records are made up of individual fields (names, addresses, or phone numbers). Figure 1-5 shows the relationship of fields, records, tables, and databases.
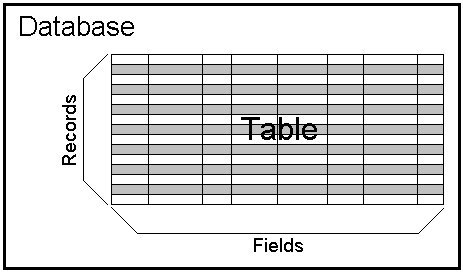 Figure 1-5 How fields, records, tables, and databases are related.
Figure 1-5 How fields, records, tables, and databases are related.
You may also hear fields referred to as columns. Within tables, Access represents fields as columns when you look at data in Datasheet view (refer back to Figure 1-3).
~~~~~~~~i will continue on my next post ~~~~~~~~~
By the time you finish this chapter, you will understand the following key concepts:
*What a database is
*How tables, forms, and queries relate to a database
*What records and fields are
*How to start Access
*The parts of the Access environment
*How Wizards can help you
*How to get help when using Access
*Possible uses for both databases and Access
*How to exit Access
1. Getting Started with Access
Access Terminology
Before you dive into the Access environment, there are a few terms with which you should be familiar. As such, we'll discuss these terms now and make sure you understand them.
What is a Database?
A database is simply a collection of related information. For example, if you gathered together all your photographs, you would have a database of photographs. If you collected all your photographs that included your dog, you would have either a more targeted database or a subset of your larger database.
If your database is small (for example, your home insurance policies), you can probably manage the information manually. In such instances, you might use a traditional management method such as a card file or a simple list on a piece of paper. However, as the database becomes larger, your management task becomes more difficult. For example, it would be virtually impossible to manually manage the customer database of a large corporation. This is where your computer and a database management system (DBMS) come in handy. DBMS software (such as Access) lets you manage large amounts of information quickly and easily.
In Access, a database consists not just of information, but also the tables into which the information is organized. Access databases also contain related queries, forms, reports, and programming instructions. Because these terms deserve further definition, they are covered in the following sections.
What is a Table?
In Access, tables contain the actual information in your database. There can be more than one table in a database. The information in each table can relate to information in other tables in your database. For example, you might have one table that contains a record of all the door locks in your building. In the same database, another table might have a list of all the keys for those locks. Still another table might contain the names of all the people who have the keys. All three tables contain related information, so they belong to the same database. Figure 1-1 depicts the relationship between the tables and this database.
 Your first step in creating a database is to determine the information you need. Next, you will use Access to design a table to hold the information. Figure 1-2 illustrates the Design view of Access. You use Design view to specify the framework used for each of your table entries.
Your first step in creating a database is to determine the information you need. Next, you will use Access to design a table to hold the information. Figure 1-2 illustrates the Design view of Access. You use Design view to specify the framework used for each of your table entries. Figure 1-2 Design view for a table in Access.
Figure 1-2 Design view for a table in Access.After you design your table or tables, you will use Datasheet view to enter and examine (view) your data. Figure 1-3 illustrates how your data may appear in Datasheet view mode.
img src="http://www.learnaccessnow.com/figs/fig0103.jpg"
Figure 1-3 Datasheet view for a table in Access.
What is a Query?
When you work with large databases, there will be times when you will want to work with specific pieces of your data. For example, if you have a company database, you may want to view the names of all your customers who reside in New York. On such occasions, you would form a query.
A query defines which database information you want to view. Think of a query as a question you ask the database, such as "Who are the customers that reside in New York?"
For example, if your database contains the names of all your customers who have purchased a particular product, your query might request a list of only those customers that made over a certain income. Another query might request only those customers with children. Essentially, a query limits or filters the information in a database. When you use a query as a filter, Access displays only information that satisfies the query.
Why would you use queries? Specifically because you want to work with only a part of your database. Queries make it easy for you to work with only those records that fit a particular criteria. Access lets you get as broad or as specific or as complex as you want in the queries you develop. You will begin to learn about queries in Chapter 6, "Using Queries to Examine Your Data."
What is a Form?
A database exists to store information. After you determine the information your database will contain, you will need to enter the data. Later, you may want to examine, add to, or change that data. Although you can use the Datasheet view to accomplish each of these tasks, you may want instead to create a custom display screen that lets you enter, view, and edit information.
Within Access, custom display screens are called forms. Using forms, you can both display the information in a table and add buttons, text boxes, labels, and other objects that make data entry much easier. Earlier, in Figure 1-3, you saw what a table looked like as a Datasheet. Figure 1-4 shows an example of a form used to input information into the same table. Notice how using the form provides a better interface for the user.
img src="http://www.learnaccessnow.com/figs/fig0104.jpg"
Figure 1-4 An example of a form used to enter information in a table.
What is a Record?
A record is a single block of information, such as employee or customer data. A table is made up of many records. For example, if you have a table that contains information about your baseball card collection, a record is the specific information about a single baseball card. Sometimes, records are referred to as rows because, within a table, Access represents individual records as rows.
What is a Field?
Just as tables are made up of records, records are made up of fields. A field is the smallest piece of information in a database. For example, if you have a table containing your phone list, each record represents a different person or business in that list. In turn, those records are made up of individual fields (names, addresses, or phone numbers). Figure 1-5 shows the relationship of fields, records, tables, and databases.
 Figure 1-5 How fields, records, tables, and databases are related.
Figure 1-5 How fields, records, tables, and databases are related.You may also hear fields referred to as columns. Within tables, Access represents fields as columns when you look at data in Datasheet view (refer back to Figure 1-3).
~~~~~~~~i will continue on my next post ~~~~~~~~~
Wednesday, November 7, 2007
Contoh Spyware
Contoh Iklan Spyware

Pernahkah anda menghadapi masalah yang sama? Biasanya pop up ni akan keluar melalui Messenger Service. Mesej yg diberikan mungkin berbeza-beza tetapi ianya tetap "Spyware" yang sama. Antara mesej yg keluar ialah seperti:
"Message from System to Alert"
"Message from system to alert stop this message"
"Message from system to alert spyware"
"Message from From to To"
"Messenger Service"
"Message from SECURITY MONITOR to WINDOWS USER"
"Message from System to User"
"Message from SYSTEM to ERROR"
"Message from Microsoft to System"
"STOP! WINDOWS REQUIRES IMMEDIATE ATTENTION"
"Your system files can be corrupted by some outer virus invasion"
"Your Windows is infected. You must choose"
Salah satu contoh mesej adalah seperti ini:
Message from SYSTEM to ERROR on MM/D/YYY H:MM:SS PM
Windows has encountered an Internal Error
Your windows registry is corrupted.
We recommend a complete system scan.
Visit
http://FixReg32.com
To repair now
p/s:So,lps ni xyah la nak buang2 msa anda melayan pop-up2(iklan yg tak dikenali) sebegini ^_^

Pernahkah anda menghadapi masalah yang sama? Biasanya pop up ni akan keluar melalui Messenger Service. Mesej yg diberikan mungkin berbeza-beza tetapi ianya tetap "Spyware" yang sama. Antara mesej yg keluar ialah seperti:
"Message from System to Alert"
"Message from system to alert stop this message"
"Message from system to alert spyware"
"Message from From to To"
"Messenger Service"
"Message from SECURITY MONITOR to WINDOWS USER"
"Message from System to User"
"Message from SYSTEM to ERROR"
"Message from Microsoft to System"
"STOP! WINDOWS REQUIRES IMMEDIATE ATTENTION"
"Your system files can be corrupted by some outer virus invasion"
"Your Windows is infected. You must choose"
Salah satu contoh mesej adalah seperti ini:
Message from SYSTEM to ERROR on MM/D/YYY H:MM:SS PM
Windows has encountered an Internal Error
Your windows registry is corrupted.
We recommend a complete system scan.
Visit
http://FixReg32.com
To repair now
p/s:So,lps ni xyah la nak buang2 msa anda melayan pop-up2(iklan yg tak dikenali) sebegini ^_^
Bahayanya Spyware (Part II)
Sambungan kepada artikel Bahayanya Spyware (Part I)
Spybot - Search & Destroy dapat mengesan dan menghapuskan pelbagai jenis spyware di dalam komputer. Kita tidak mudah untuk mengetahui sama ada komputer kita di jangkiti atau tidak kerana sudah menjadi sifat spyware beroperasi secara tersembunyi tanpa pengetahuan mangsa. Tetapi dengan menggunakan Spybot S&D, komputer kita akan selamat daripada 95% spyware. Dan yang paling penting, Spybot S&D adalah project & perisian percuma. Selain spyware, Spybot S&D juga dapat menghapuskan dialer, Keylogger, Trojan Horse & Usage Tracking.
Jika anda adalah pengguna Internet yang tegar, download & install Spyware - fixcrakerz.
Spybot S&D adalah keperluan bagi setiap pc. Kemaskini spyware seminggu sekali. Mari bersama membenteras SPYWARE! ^_^
Spybot - Search & Destroy dapat mengesan dan menghapuskan pelbagai jenis spyware di dalam komputer. Kita tidak mudah untuk mengetahui sama ada komputer kita di jangkiti atau tidak kerana sudah menjadi sifat spyware beroperasi secara tersembunyi tanpa pengetahuan mangsa. Tetapi dengan menggunakan Spybot S&D, komputer kita akan selamat daripada 95% spyware. Dan yang paling penting, Spybot S&D adalah project & perisian percuma. Selain spyware, Spybot S&D juga dapat menghapuskan dialer, Keylogger, Trojan Horse & Usage Tracking.
Jika anda adalah pengguna Internet yang tegar, download & install Spyware - fixcrakerz.
Spybot S&D adalah keperluan bagi setiap pc. Kemaskini spyware seminggu sekali. Mari bersama membenteras SPYWARE! ^_^
Bahayanya Spyware (Part I)
Apa itu spyware? Spyware adalah perisian kecil (small software) untuk mencari maklumat di dalam pc melalui internet connection tanpa pengetahuan mangsa (pemilik pc tersebut), selalunya bagi tujuan pengiklanan. Spyware biasanya terselit bersama perisian Freeware atau Shareware yang boleh di muat turun (download) melalui internet. Tetapi bukan semua perisian Freeware atau Shareware mengandungi spyware (sebahagian kecil saja). Apabila spyware wujud di dalam pc, spyware ini akan memantau setiap aktiviti melalui internet dan akan menghantar maklumat yang diperolehinya(di belakang tabir) tanpa pengetahuan mangsa (victim) kepada seorang(pembuat spyware) tersebut. Spyware boleh mencari maklumat mengenai e-mail, password & no. kad kredit.
Spyware menyerupai Trojan Horse. Seseorang individu tidak akan mengetahui wujudnya spyware di dalam pc selepas install sesuatu perisian. Biasanya perisian-perisian yang dibeli (bukan original) & download melalui internet adalah berpotensi mengandungi spyware di dalamnya. Pengguna internet yang kerap menggunakan perisian peer-to-peer adalah berpotensi untuk menjadi mangsa spyware.
Spyware juga dapat mencuri maklumat melalui memori komputer dan bandwidth internet. Oleh sebab itu, spyware boleh menyebabkan sistem komputer rosak (crash&nuke) atau sistem menjadi tidak stabil. Kebanyakan spyware tidak dapat di kesan oleh perisian anti-virus biasa.
Antara tanda pc mengandungi spyware ialah, apabila kita membuka web browser (biasanya Internet Explorer), kita akan dibawa ke web iklan. Ataupun terdapat tanda-tanda di mana pc kita tidak lagi berfungsi seperti sediakala (selalunya berkaitan dengan kelajuan pc, di mana pc menjadi semakin lembab).
Spyware menyerupai Trojan Horse. Seseorang individu tidak akan mengetahui wujudnya spyware di dalam pc selepas install sesuatu perisian. Biasanya perisian-perisian yang dibeli (bukan original) & download melalui internet adalah berpotensi mengandungi spyware di dalamnya. Pengguna internet yang kerap menggunakan perisian peer-to-peer adalah berpotensi untuk menjadi mangsa spyware.
Spyware juga dapat mencuri maklumat melalui memori komputer dan bandwidth internet. Oleh sebab itu, spyware boleh menyebabkan sistem komputer rosak (crash&nuke) atau sistem menjadi tidak stabil. Kebanyakan spyware tidak dapat di kesan oleh perisian anti-virus biasa.
Antara tanda pc mengandungi spyware ialah, apabila kita membuka web browser (biasanya Internet Explorer), kita akan dibawa ke web iklan. Ataupun terdapat tanda-tanda di mana pc kita tidak lagi berfungsi seperti sediakala (selalunya berkaitan dengan kelajuan pc, di mana pc menjadi semakin lembab).
Subscribe to:
Comments (Atom)